Better for users. Easier for IT. Safer for everyone.
Get secure access to any application, on any device, from anywhere, to support zero trust with zero friction.
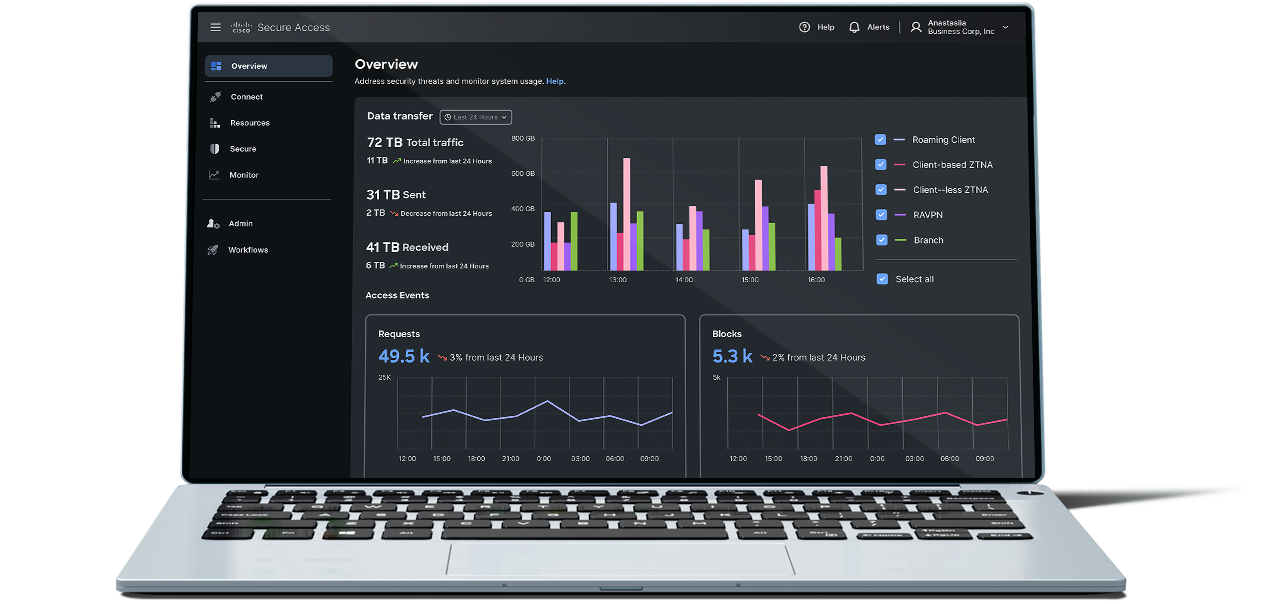
Secure any user, on any device, from anywhere
Choose from 2 easy-to-adopt User Protection packages
User Protection Essentials
Essentials
Deliver streamlined security that frustrates attackers and not users. Easily protect against threats, reduce risk and complexity, and improve the user experience.
What's included:
User Protection Advantage
Advantage
Reduce complexity and improve visibility across your entire environment. Proactively block more threats while providing seamless, secure user access from anywhere.
Products in the Advantage tier include and build upon products within the Essentials tier.
What's included:


